Cryptography in Blockchain
In this article, we will learn about blockchain, Cryptography in Blockchain, its types, hash functions, digital signatures etc. Let’s start with what is blockchain?
About Blockchain Technology
Blockchain technology refers to a tamper-resistant digital ledger (or database) distributed on a network that operates without a central authority. It relies on a peer-to-peer network, instead of a central authority for the decision-making process.
The name blockchain is made using two words – block & chain. A block is a collection of data, alias data records, and the chain refers to a public database of these blocks, stored as a list. These lists are linked together using cryptography, which makes them highly secure and tamper-resistant.
Significance of Security for Blockchain
We have discussed how cryptography makes blockchain more reliable and secure but why exactly are those qualities needed? Let us understand the significance of security in blockchain.
Blockchain is designed to be a decentralised distributed database, meaning that it will have to store and maintain a large number of data. Today, data theft is on the rise and as common people are beginning to understand how multinational corporations can misuse their sensitive data, data privacy and security are in the mainstream.
In such a scenario, blockchain offers secure data storage in digital databases that are not controlled by any authority, and reliable. These databases also offer the option for trackability, and this transparency allows anyone to verify the immutability of the blockchain. This security is ensured by cryptography which safeguards user transaction information and privacy.
Cryptography in Blockchain
Cryptography means developing techniques or methods to prevent an outsider from accessing or understanding data from a private message. Let’s review some terms related to cryptography :
1. Encryption: Process of converting plaintext to a ciphertext (random sequence).
2. Decryption: Conversion of ciphertext to plain text; inverse of encryption
3. Cipher: This is the cryptographic algorithm that was used in encryption
Hence, cryptography basically involves sending encrypted messages across a secure channel which are then decrypted in order to obtain the real message. The sender encrypts the message using an algorithm and a specific key, which will be used by the receiver to carry out the decryption of the encrypted message.
These keys are vital to ensure that unauthorized or unwanted individuals/organizations are unable to access the message, data or transaction. Thus, these keys bring the crypto aspects to our information.
Types of Cryptography in Blockchain
Over the years, cryptography has been of utmost importance to secure important documents through the course of history. Hence, we have a number of types of cryptography that vary according to algorithms used, like :
1. Symmetric Key / Secret-Key Cryptography: Popular encryption method that involves a single key used in both encryption and decryption.
2. Asymmetric Key / Public Key Cryptography: This method involves a pair of keys, public key (for encryption) and private key (for decryption). Both the keys are generated using the same algorithm.
3. Hash Functions: This is a different kind of method that does not involve any key. Cipher is used to generate a hash value of a fixed length from the plaintext. It is highly secure.
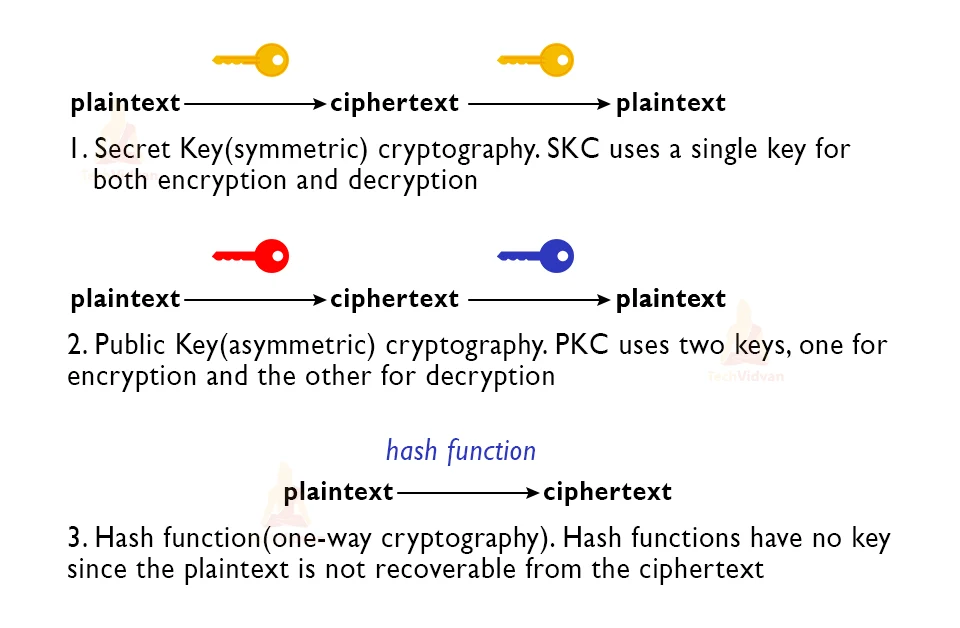
Understanding symmetric key encryption
This is a basic form of encryption that focuses on using similar keys for encryption and decryption. It is in fact, popularly used in IT security services like hard drives and HTTPS websites. The use of similar keys is also referred to as secret key cryptography.
To understand using an example, imagine you and your friend live in the same house. To ensure the house is protected from burglary you lock the house whenever you both have to go out and take the key with you. But, one day your friend has to come home early, so you share a spare key with your friend, it is exactly like your own key and can be used to open the same lock. No other lock can be opened by the key, and only someone who has the key can open the lock.
Understanding asymmetric key encryption
This is really important in blockchain and is also referred to as public key cryptography as it involves a set of 2 keys one each for the encryption and decryption processes.
The public key can be shared publicly to allow easy and feasible data encryption while the private key has to be kept a secret so that unauthorized persons do not get access to the decrypted data.
Cryptography in Blockchain
Blockchain technology employs both hash function and asymmetric key cryptography. Asymmetric key cryptography is also used in blockchain. Here, the private key is produced by a random number and the public key is calculated by an irreversible algorithm.
The 2-key authentication system makes it more secure and resistant to attacks. Blockchain uses this method for Digital Signatures. These provide integrity to the data transfer process, and are proof that the data has not been altered, hence often termed as digital fingerprints too because of their uniqueness. Hash functions are used to allow all participants to view the blockchains. The SHA-256 hashing algorithm is the most preferred for this purpose.
Role of cryptography in blockchain
Hash functions and asymmetric keys allow secure data transfer and storage in a blockchain. In fact, hashing allows data storage in a way that it is impossible to generate the input even if output is known. Hence reverse engineering is impossible. The technology is deterministic, thus a particular input will always give the same output and a slight change in the input will drastically alter the output.
SHA 256
This is a hashing algorithm where SHA stands for Secure Hash Algorithm.
Hashing is the process of scrambling raw information to the extent that it cannot be reproduced to its original form. The process takes the plaintext and passes it through a function that performs mathematical operations to convert it to ciphertext. This function is called the hash function, and the output is called the hash value/digest. SHA256 refers to the fact that the hash digest at the end of this algorithm will always be of 256 bits.
Characteristics of hash functions
1. Deterministic: Slight change in the data drastically changes the output
2. Unique output: Each input value has a unique output, but any input will have the same output.
3. Irreversible: The input cannot be generated even if we had access to the output and hash function, hence no reverse engineering
4. Fast Computation: Very quick encryption.
Hence, hash functions are used to link blocks to one another and maintain data integrity inside a block. If data inside a single block is altered or tampered, the chain will break and the blockchain will become invalid.
Benefits of a cryptographic hash to a blockchain
1. Prevents unauthorized modifications
2. A slight change in the input will drastically alter the output
3. Verification of transactions
4. Access to proof of ownership of specific information without revealing the information.
Understanding Digital Signatures in blockchain
Digital signature basically refers to a mathematical approach for creating digital codes which are used to verify if a digital message (or documents) is valid or not. Digital signatures can be considered as proof for the authentication and non-repudiation of the blockchain. They address the requirements of data integrity, immutability and authentication. Effectiveness of blockchain cryptography and these digital signatures depends on symmetric and asymmetric key encryption.
Conclusion
In this article, we familiarise ourselves with the basic concepts of blockchain and cryptography. We learnt the different types of cryptography that are popular and the ones used in blockchain specifically and the benefit of using them.
