Communication Protocols in IoT
IoT works mostly with IPv6 which is the latest internet protocol version and it is used for transferring data and communication. Each IoT device has an IP address and networking is the key aspect in the Internet of Things. Communication layer provides service to the network layer. In this article we will look at a detailed explanation of most common communication protocols followed in the IoT.
Communication Protocols in IoT
1. Link Layer protocols
The top five protocols in the Link Layer are Ethernet, Wifi, WImax, Low rate WPAN and mobile communication such as 5G, 4G and 3G. PHY and MAC protocols use this layer.
2. Network Layer protocols
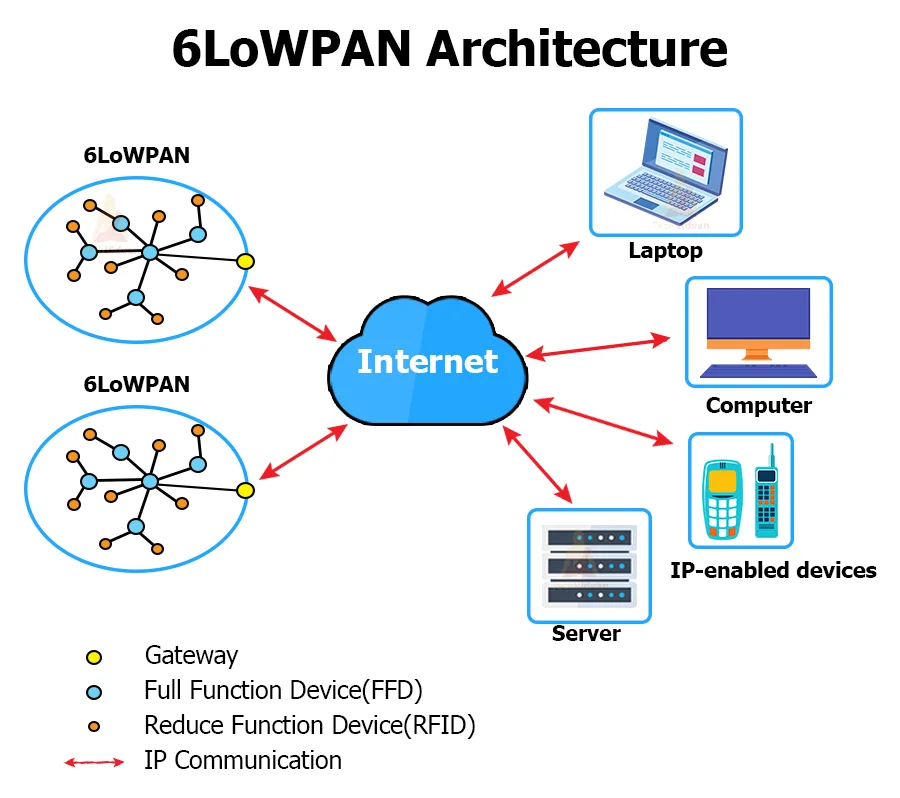
This is an important layer. The protocols used in this layer are IPv4(used previously), the recent IPv6 layer handles 128 bit addresses and 6LoWPAN. 6LoWPAN is called the adaptation layer.
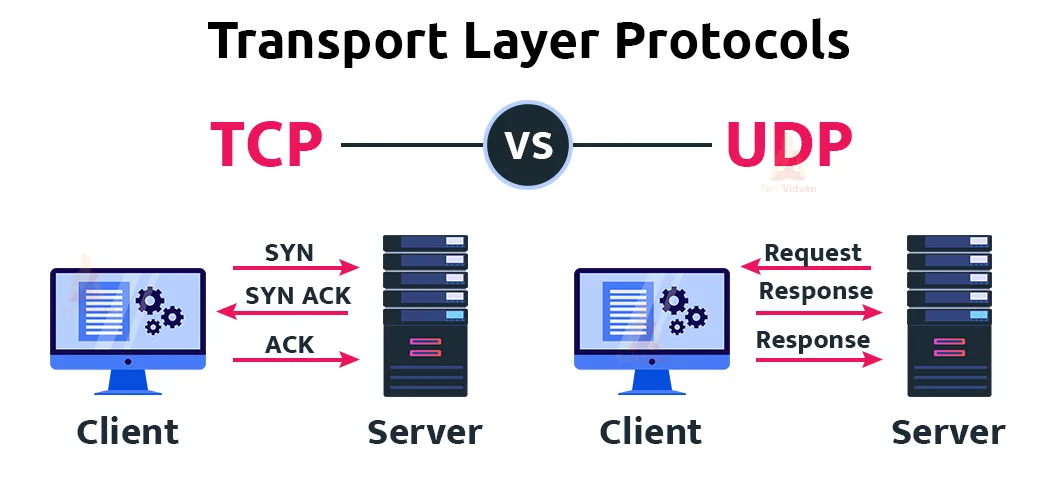
3. Transport Layer protocols
This layer contains the transport agents. This layer has two main protocols – TCP(Transmission control protocol) and UDP.
a. TCP – It is highly reliable and it has error control, control flow and congestion control. There is no packet loss as each packet sent expects an acknowledgement in return. Flow control takes place when the receiver adjusts its size and sends packets based on the window.
b. UDP – It has a very simple implementation. Usually, audio and video datas are sent via UDP. In this protocol, acknowledgement is not needed since all the packets are sent from the same parent. It is IoT friendly.
4. Application Layer protocol
This is the most important protocol. This layer provides service to the users. It gives information to the user. This layer is essential as it is capable of serving the needs of the user. For example, if a user wants to know information about the temperature flow of his smart refrigerator. This layer sets the messaging capacity and concludes the performance of the service. These layers mostly fit into the standard of IoT compared to the pre-IoT era.
The common protocols in this layer are as follows:
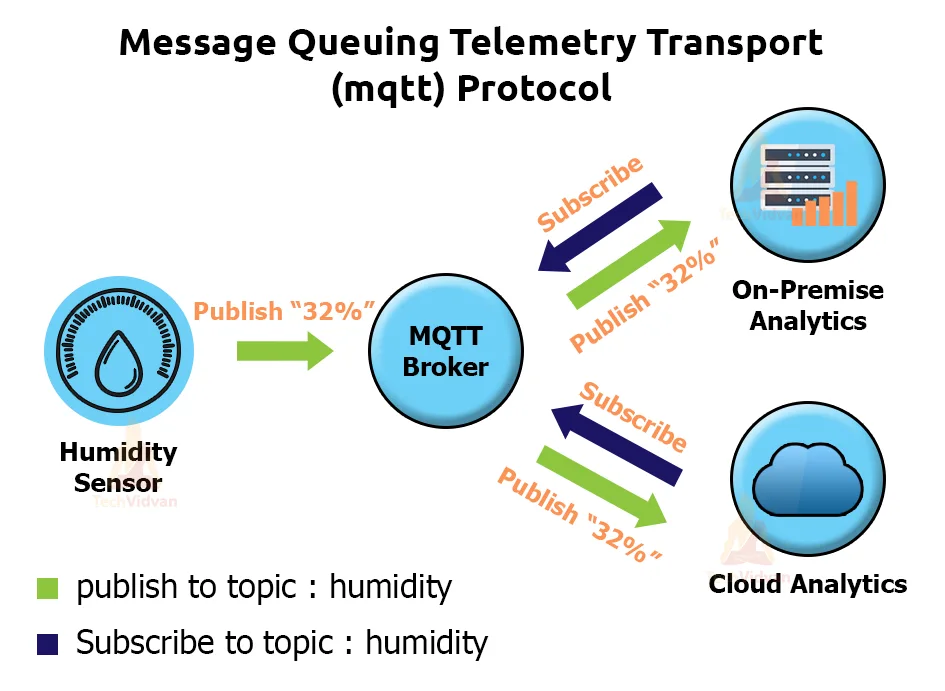
a. MQTT Protocol in IoT – Message Queuing Telemetry Transport
MQTT is suitable for vehicle to vehicle automotive communication. It is practised in most of the European countries these days. It uses a publishers-subscriber model that is adapted from the client-server model. The servers that run MQTT are gateways.
So there are four main components involved in this model.
- The publishers publish the message or rather subscribe to a topic.
- The MQTT server manages the incoming message and sends it over to the subscriber clients.
- The broker acts as a storage component and stores all the messages from the subscriber client.
- Each topic has a label for identification. Next, the client sends the relevant subscription with one or more topics.
The subscriber/publisher method relies on the MQTT control packets.
b. Secure Message Queue Telemetry Transport(SMQTT)
This protocol is an extended version of the MQTT protocol. It works on light weight attribute encryption. It enhances the security features of MQTT protocol. Encryption converts your information or data into a specialized code to prevent hacking and illegal access to your private. This is a necessary feature in IoT devices since there is a constant transmission of data. SMQTT ensures a safe data transfer between two devices, clients and servers.
Its algorithm consists of: initialization, encryption, publishing and decryption.
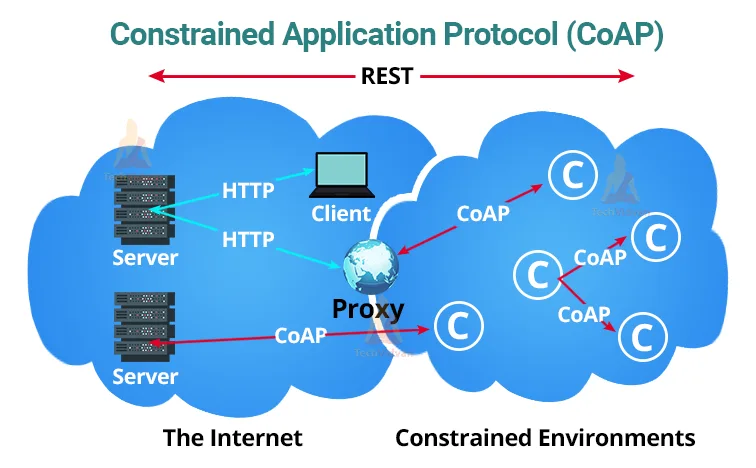
c. Constrained Application Protocol(CoAP)
Constrained Application Protocol specializes in web transfer protocol and as the name suggests it is used in constrained networks and constrained nodes. They are generally used in sectors such as smart energy and building automation.
It follows the client-server protocol which is also the protocol in HTTP. Just as the protocol in HTTP, the client sends a request and the server responds to the request. HTTP methods such as GET, POST, PUT and DELETE find their relevant use in CoAP as well.
The communications can occur between client and client, server and client and between client and server via a proxy. Proxy serves as a gateway to forward messages between server and client.
In CoAP, a smart “thing” is capable of acting both as a server and client. A client sends a request for a server resource through a method code.The server replies with a respond code.
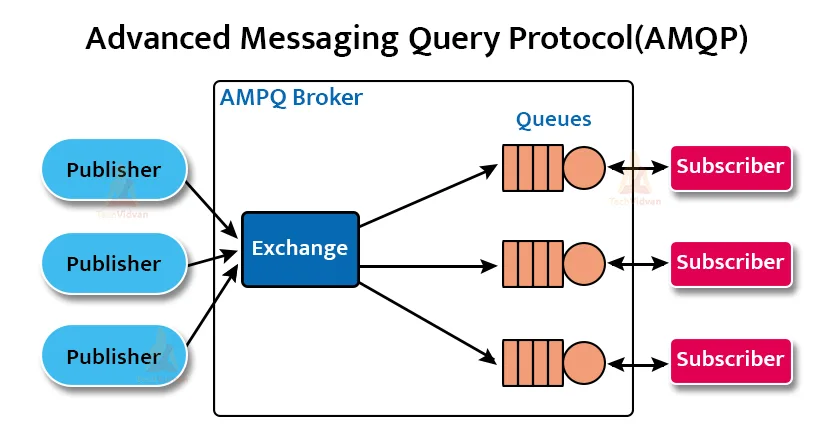
d. Advanced Messaging Query Protocol(AMQP)
The necessity of solving core technologies has given rise to the AMQP protocol. The main goal of AMQP is to be practical, reliable and useful. It targets to spread message oriented middleware across. It brings users and vendors together to solve all the existing, common problems. Usually, we label AMQP as “Internet Protocol for Business Managing” so the end users feel a connection to technology without a sense of being left out.
In this protocol, on one side we have the clients on the other side we have the service. The services communicate using an AMQP bus and all the code is written mostly in C++ or Java.
An AMQP broker has three components:
1. Exchange receives the messages from published and then forward these messages.
2. Queues saves these messages and then sends it over to the subscriber.
3. Binding acts as an intermediary between queue and exchange. It connects the exchange to the desired queue.
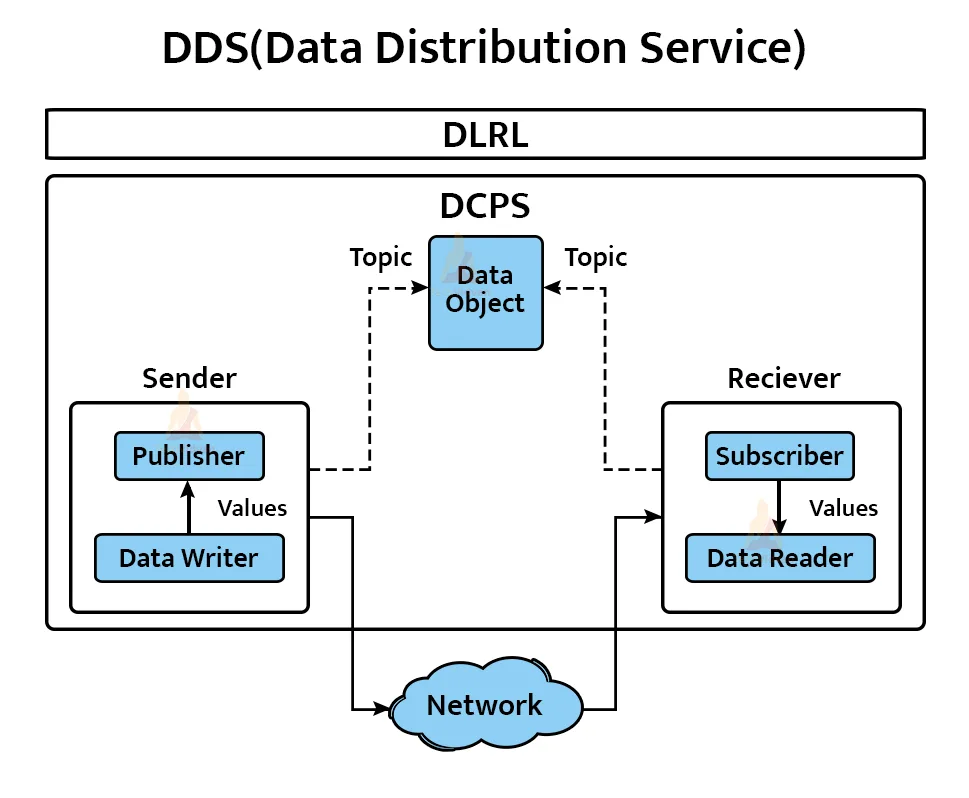
e. DDS(Data Distribution Service)
This architecture varies from the ones discussed above as DDS is a brokerless architecture. Publish-subscribe communication architecture makes up the architecture of DDS. Object Management Group (OMG) executes the DDS.
Its message model divides into two types:
1. Data centric Publish Subscribe(DCPS): DCPS layer provides messaging ability. It is the main core of DDS.
2. Data-local Reconstruction Layer(DLRL): DLRL is an additional layer that is not necessarily added. It manages application integration and at times provides highly advanced features.
The DDS provides high performance over transport protocols and platforms. It is widely used in companies such as Google, IBM and Microsoft.
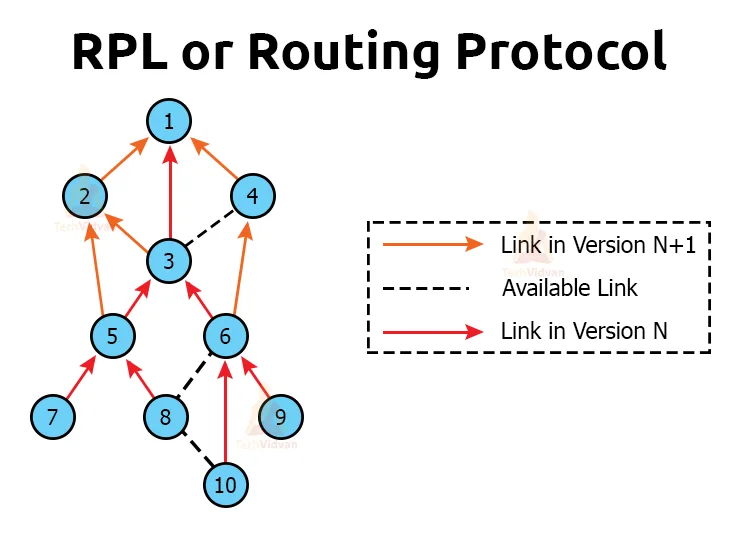
f. RPL
RPL or ROuting Protocol for low-power Lossy networks is long distance routing protocol which is conditional to DODGAS( Destination oriented acrylic graphs). It is a type of graph that contains no cycle such as the spanning trees. In this tree, each node wants to reach a single destination. This protocol has chances of packet loss.
Dodag Information Object(DIO) is a multicast message by any given node. It lets other nodes know about the status.
Dodag Information Solicitation is a message that a node sends if it wants to join the Dodag.
DODAG advertisement object(DAO) are requests from child node to parent node and DODAG-ACK are responses from parent node to child node.
g. CORPL Protocol
This is the extension of RPL protocol and it is known as cognitive RPL protocol. It uses the same DODAG topology as we have seen above. It’s design fits cognitive networks. Nodes forwarded packets through opportunistic forwarding. The difference is that, in this protocol each node has the information instead of only the parent. Every node uses DIO messages to update each and on this basis they construct the forwarding set.
h. CARP
CARP also known as Channel Aware Routing Protocol has light weight packets. Underwater communication and IoT technology use this protocol mostly. It does not support forwarding technologies and security. On the basis of link quality from the data history of transmission, it selects the forwarding nodes.
The two steps in CORP routing are initialization and data forwarding. During network initialization, it broadcasts from sink to the rest of the nodes. E-CARp is an upgrade to CARP.
i. 6LoWPAN
This protocol connects the IPv6 with 802.11 and IoT devices. Thread is a perfect example of the application of 6LoWPAN.
j. Radio protocols
Radio protocols create low-power and private area networks and the most common are Zigbee, Z-Wave and thread. They use less power but generate quick results. They are cheap yet raise the standard of small local device networks.
i. ZigBee
Zigbee is a very popular IoT protocol. It has 2.4 Ghz frequency which is popularly used worldwide. Zigbee suits high level communication protocols. It supports Zigbee Green power devices that work effectively in energy harvesting.
Energy harvesting is a process in which you extract energy from the environment in the form of vibration, light, wind or through water. We convert these sources into energy that powers a large amount of devices. For example, sunlight is used to power solar panels that provide electricity.
LoRa(low range)/LoRaWAN
This is a popular protocol in the industrial sector. It finds its use mostly in industrial IoT. LoRa is a standardized protocol used in devices and boards to construct IoT devices.
LoRa is the wireless link and LoRaWAN is the communication link on the other side of the wireless link. It gets back to an IoT Network such as an application or a server. It deals with situations in the physical layer whereas LoRaWAN deals with situations at the upper layer.
They contain different classes of devices: class A,B and C.
Class A contains battery powered sensors, class B contains both battery powered sensors and actuators and finally class C are main-powered actuators which are plugged into some form of power. The difference in operation is done on the basis of how these devices operate with and without power.
ii. Z-wave
Z-wave is another communication protocol and its common uses include smart home networks. It allows devices in a smart home to connect to each other. It is low cost and wireless communication. This allows devices a two-way communication via a mesh network and message response. It uses less power compared to WiFi and uses longer-ranges like Bluetooth.
Bluetooth and BLE
It reduces the cost, power usage and maintenance cost by a wide factor and hence it is commonly in use. Bluetooth special interest group or Bluetooth SIG manages Bluetooth.
The recent introduction of Bluetooth Low energy uses low power consumption. Beacons does the job of locationing. With Bluetooth 5.0, Direction finding and Mesh were brought into motion and it is widely used these days.
Bluetooth steps up its game constantly due to the introduction of a lot of highly technical enhancements. It is gaining wide popularity and soon it may become a margely common IoT protocol. It has lots of potential in the coming future.
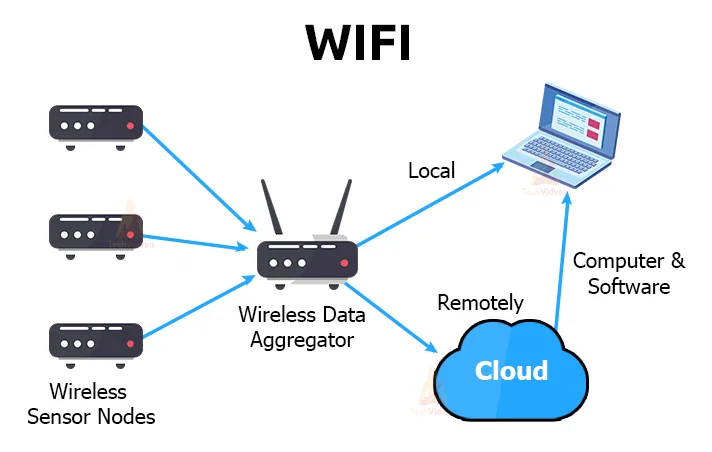
iii. WiFi
Wifi is another frequency or radio protocol that connects wirelessly to devices. It is a replacement to ethernet which requires wires. Wifi transmits data at frequencies of 2.4 Ghz and 5Ghz. It supports broadband and narrowband applications. It supports IoT applications that require high bandwidth and latency.
Cellular Network
Cellular network is the most stable connectivity technology that works well and is highly reliable. LTE-A is an advancement to the LTE technology. It highly increases the coverage and reduces its latency. It is of much use in IoT in applications such as cars and UAV.
Service Provider Network
This is a common option for IoT technologies. It also grants standard mobile phone access, Laptops and tablets, it also provides backup internet connections through LTE/5G routers and it also offers mobile vehicular access and fleet tracking.
Private Network
There is a lot of buzz around private LTE and private 5G of the private network these days.
NFC and RFID
- NFC or Near Field communication connects powerless devices. Embedded NFC in powerless devices helps you add intelligence anywhere. NFC is simple to use and connects users easily. You can easily connect to the network and start sharing data. NFC also offers device and network security.
- RFID or Radio frequency identification uses a two-path radio to identify and follow objects with tags.
iii. Thread
Thread is a low-power, wireless communication protocol that operates through mesh networking. It can connect hundreds of devices and offer them security and safety. It is also capable of reconfiguration and self-heal in case of threats. Thread offers easy connections, supplies a flexible platform and easily integrates with large networks.
NB-IoT
Narrow Band IoT is a 5G technology whose design fits networks that require low bandwidth or bear dense connections. Coverage is extensible in the system including low latency and also covers real-time security and protection.
Rural and deep indoors are common applications of NB-IoT. The ultra-low device complexity allows it to connect to large amounts of devices in a single disposal. It has an extensive battery life, it is highly disposable and reliable.
5. Network protocols
Network protocols transfer and share data in a safe and easy manner. Open Systems Interface put forward by ISO is the most common way to lay communication between two open systems.
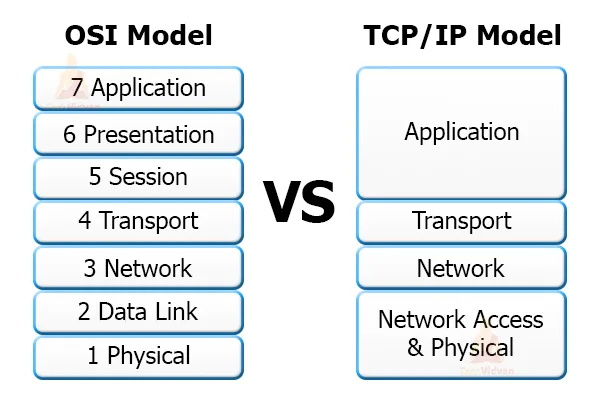
a. OSI model
The OSI model just guides every layer and explains its input and output data. Network architects then use these definitions accordingly.
There are seven layers in the OSI model- Physical, network, datalink, Transport, session, Presentation and finally application. TCP-IP model implements OSI. TCP-IP simplifies the seven layers into a four layer internet protocol.
1. Physical Layer: As the name suggests, one may find physical devices such as cable and modem at this layer. It transports raw and unfiltered data. It sends and receives data.
2. Data Link layer: It has constrained nodes that transfer data and information among other nodes. Media Access control(MAC) offers flow control and multiplexing. Logical Link Control(LLC) offers flow and medium control and recognized line protocols.
3. Network Layer: This layer receives information from the data link layers and based on the instructions and address written in them, it passes on the information accordingly.
4. Transport Layer: This layer delivers the information and checks for eros in the data. TCP is one such example of this layer.
5. Session Layer: This layer sets up and manages a connection between machines. This layer also authenticates and reconnects.
6. Presentation Layer: This layer interpretes data for the application layer on the basis of syntax and semantics the particular application accepts.
7. Application layer: This layer interacts with the end user and the software. It provides services to the end-user, for example, office360.
b. TCP/IP
The TCP/IP layer combines some of the OSI model layers and contains four layers.
1. Network Access and physical Layer: This layer combines both the first and second OSI layers into one. This layer establishes connections and assigns each device and IP address for ease of recognition.
2. Internet Layer: This layer tells how routers deliver data packets from host and source destination on the basis of IP addresses.
3. Transport Layer: This layer ensures that the packets are sent in the same path from which they arrive.
4. Application Layer: This layer ensures application level messaging. Examples include HTML and FTP.
c. FTP File Transfer Protocol
IoT transmits files from one destination to another constantly. FTP or File Transfer Protocol handles requests of file transfers in the given network. The following are the features of FTP:
- Transfers files between any given networks
- File transfers takes place even during connection drops but the protocol configuration should be correct
- Separate team can collaborate geographically
d. PPP Point to Point Protocol
PPP is a standard method responsible for transporting basic transfer units through point-to-point links. It contains three main components:
- A method that encapsulates the transfer units.
- An LCP or Link control protocol for setting up, configuring and testing data-link connections.
- NCP National Control Protocols for setting up and configuring the network layer protocols.
Conclusion:
In this article we took a look at the various communication protocols in IoT that are most common such as Link layer, network layer, transport layer and application layer.