IoT Security Issues and Solutions
In this article we will talk about the security of the IoT (internet of things). So let’s begin.
Introduction to IoT Security
Security in Iot systems is a growing concern. IoT has a lot to offer and has a potential future but more than often the question of safety and security in IoT systems arises. IoT, once a scientific phenomenon, is now in use by billions of devices world wide.
We find IoT in homes, cars, offices and even cities. But the problem lies in the security. Many of the devices have poor and unsafe functionality and cybercriminals are taking advantage of this. It is very easy for ethical hackers to enter a person’s network and gain access to all personal details.
IoT devices are being used in DDoS (Distributed denial of service attack). If a device is capable of communicating with other devices then there is always a chance of it being hacked and providing a way to the network the device is connected to.
What is IoT security?
The segment of the internet of things that focuses on protecting the IoT system, servers, networks and physical devices is known as IoT security. It involves using methods, tools and strategies that benefit the users and protect the IoT ecosystems. The growing concern of Iot exposure to large numbers of malware attacks gave rise to IoT security. Some of the methods IT developers use to secure IoT systems are PKI, end-to-end encryption and API security.
Why IoT security?
Through IoT security, it is possible to prevent all types of attacks and vulnerabilities in any IoT system. Developers use technologies, methods and devices to prevent security breaches. Cryptography technologies fight communication attacks whereas security services battle lifecycle attacks. Developers make use of isolation measure to prevent software attacks and tamper mitigation methods to avoid physical device attacks
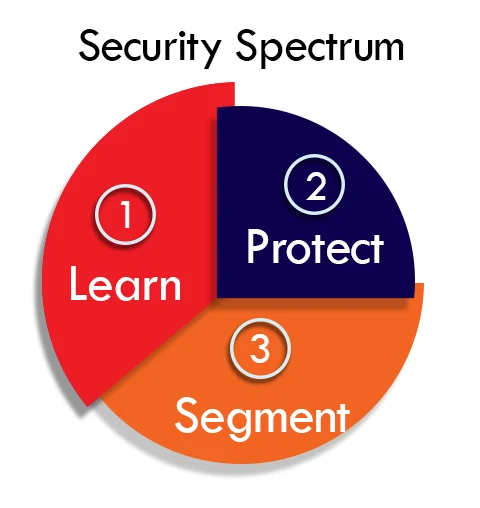
Security spectrum
IoT security involves the protection of physical devices and networks. It includes the measures, impacts and technologies used to protect IoT devices. Security can be seen as a spectrum that evolves as the technologies evolve. Devices with upgradation are less prone to attacks as compared to older, poorly secure devices.
Secure devices must include simple to complicated designed devices. The security of a system is built based on the users needs and implementations. Any user must fully understand the impact of a security breach and must be able to recognize malware attacks at an early stage to avoid serious damage
Types of vulnerabilities
Iot device security aims to protect the information, devices and networks from cyber criminals that target our types of vulnerabilities:
- It involves protecting the communication lines between users and web servers. Protecting the devices when it changes state from user to maintenance mode.
- Security breaches in the internet of things software
- Direct physical devices that target the chip inside the Iot devices.
Challenges faced by IoT systems
1. Unpredictable conduct
There is a huge amount of deployed devices with enabling technologies. This means that their behaviour in any sector can be unpredictable. The system may have a proper design and structure with a reformed administration but one cannot predict its interaction with other systems.
2. Similar devices
There are not many options for IoT devices and most of them are fairly similar. They make use of the same connection and network protocols. If one device gets a DDoS attack, it affects the rest of the devices too.
3. Difficult deployment
Deployment is a difficult process in IoT devices considering the fact that there are too many devices with internet connection.
IoT aims to advance to areas and networks where it was impossible to enter before. These devices produce data every second. This creates difficulties in deploying devices.
4. Long device life and expired support
One of the major advantages of IoT devices is their extremely long life. However, this could mean that the working of IoT devices extends beyond their support and warranty periods. These devices lack security and are open sights for cybercriminals.
5. No upgradation support
Upgrades and modifications are not possible in many IoT devices. Many times the upgrades are difficult to enforce or go unnoticed by the users.
6. Poor or zero transparency
Iot devices have a reserved functionality, meaning there is no access to the inner working of IoT devices directly.
Users can only assume the working of their devices as access to the inner components is not possible. They cannot control the data flow and information collection which leads to obtaining unnecessary information by the device.
7. No alerts
There is no alert system to warn users about malware. Hackers use this setback as an opportunity to gain access to the network of the Iot device and obtain personal information. IoT is currently working on improving the safety of its devices.
Security issues in the IoT system
Threats and risks
1. Vulnerabilities
Unsafe devices are a big threat to IoT systems. Unguarded devices are open to a number of threats by hackers and cybercriminals. IoT devices do not have the computational capacity to offer in built-security and this leads to unsafe IoT systems that are under threat constantly.
2. Malware
Cybercriminals mostly use malware to attack Iot systems. Iot botnet malware is the most popular variant that hackers use to gain access to private IoT ecosystems. The limitation in computational capacity of IoT devices causes malware infections.
3. Cyberattack escalation
Distributed-denial-of-service attacks often use infected devices. One hijacked device can provide access to other web servers and networks. In this case, it gets difficult to recognize the entry point to stop further loss.
4. Information theft and unknown exposure
As devices connect to the internet online, their chance of leaking private and sensitive information increases. Systems can store private details about its customers and users.
5. Device mismanagement and misconfiguration
Overseeing security, maintaining the same or poor passwords and updated software are few of the many reasons that contribute to IoT security attacks.
Emerging issues
Industry foresight helps in identifying emerging issues in order to define and develop strategies. Given below are few emerging issues one must monitor:
1. Complex environments
Complex IoT environment is the use of more than 10 Iot devices in any particular household. With the rise in IoT devices, environments like these become difficult to manage and monitor.
2. Prevalence of remote work arrangements
The users who work in companies with remote work arrangements are more prone to attacks as the users use home networks that may be less secure as compared to enterprise networks.
3. 5G connectivity
5G connectivity is a recent technology and most of its functionality is yet to be discovered. There is much expectancy for 5G transformation to offer more safety and connectivity.
What should you know about IoT security?
Interconnected devices can uplift any business. But any device that connects to another device to share information is also prone to cyberattacks. It is important that we understand device protection, antiviruses and cybersecurity in order to make our networks, servers and devices free from criminal exploitation.
1. Tabs on mobile devices
Users must ensure that there are locks and passwords on mobile phones and tablets. One can easily access information from a missing electronic device. But it is harder to access a locked device. Trackers can track and provide the exact location of a stolen electronic device.
2. End-to-end encryption
Data transfers take place when one device communicates with another. In order to ensure that this communication is safe, you need to ensure end-to-end encryption.
3. Select an expert cybersecurity provider
Cyber Security and antivirus providers offer softwares that protects companies against threats and vulnerabilities that can potentially damage the entire enterprise.
Additional IoT security methods
Following are the additional way to implement IoT security:
1. NAC(network access control): NAC recognizes all the devices in a certain network. This helps in monitoring and tracking devices easily.
2. Segmentation: We can segment the network of each of the iot devices that connects to the internet and we can limit the access to the business network. One must monitor the network for unidentified access.
3. Security gateways: Security gateways offer more power to the system by acting as an intermediate between iot devices and the network itself. Properties such as firewalls make sure that hackers do not hack IoT devices.
4. Patch management/continuous software updates: It is important to update Iot devices regularly by means of network or automation. Un updated devices are open to a large number of vulnerabilities
5. Training: Training and introducing the IoT staff to certain security terms is crucial. IoT is a fairly new technology and developers may not be well versed with the functionality. Therefore, the security staff must undergo proper training.
6. Integrating terms: The security analysts and software developers must work in the same environment as a team to ensure better production.
7. Consumer education: Finally, IoT is a recent technology. Consumers and users have less idea about its working. If the users are more aware of their Iot purchases we can ensure more safety overall.
Which industries are most vulnerable to security threats?
Any industry is prone to iot security attacks and no system is completely secure. Hackers always find loopholes and breaches and thus we must ensure that there is maximum security to prevent access. Anything ranging from a smart home, smart car to a smart grid is under threat.
The severity of any attack depends on how much information the sensors collect, the servers and the extension of the network. Attacks could be life threatening such as in smart healthcare. Attacks could also cause potential accidents such as in smart cars.
Some security breaches may not be very serious also. For example, if cybercriminals obtain access to smart lock, a change in the entire lock system prevents serious damages.
How to protect your IoT devices?
There are some ways that can guarantee security. But no device is completely secure. We can only try to obtain maximum security.
Given below are few of the many ways to ensure your IoT device is safe.
- Make sure that you are fully aware about the nationality of each of the IoT devices you own.
- Make sure the devices are up to date and discard any old devices.
- Always use strong and unique passwords.
- Before buying an IoT device, make sure to read about the manufacturer’s reputation and security.
- Most of the attacks can be avoided by introducing protection in the beginning stages of production.
- In multiple networking systems, PKI ensures security between client-server devices.
- Securing the API is crucial in any IoT system since API is the backbone of an IoT solution.
- Invest in a good antivirus software. Antivirus softwares takes care of all the complicated processes and makes sure your system is out of danger.
Consequences of security attacks
The impact of any attack on the IoT system can be more damaging than one can possibly imagine. Since Iot systems involve physical and virtual components, any cyber attack can equally impact the physical devices.
For example, an attack on an IoT healthcare system can release sensitive and private details about the patient to the outside world. And an attack on a smart home could expose the entire household, assets and valuables. Since IoT devices communicate via a network, the whole network could be unsafe and eventually the entire server is exposed to attacks.
Summary
So, in this article we read about the internet of things security and what it stands for. We learnt about the security spectrum and the various types of vulnerabilities. We further look at the challenges an IoT system faces in terms of security. And finally we look at a few measures to protect your IoT devices. We hope you liked our explanation.