IoT vs M2M – Difference Between IoT and M2M
In this tutorial, we will learn about IoT and M2M and IoT vs M2M. Let’s start!!!
M2M stands for machine-to-machine communication. It allows devices with wireless connections to directly communicate with each other without any human involvement. M2M stores the data incoming and sends it to other devices. It is a form of technology that offers devices to communicate without any internet requirement. Some of the most common uses of M2M are tracking, monitoring, controlling, defense and management.
M2M allows users to capture, store and send data from one device to another. This allows users to remotely monitor their assets, manage and run organizations, or simply offer connectivity to devices with remote connections. M2M however, does not allow a broader sharing of data or connection of devices.
What is IoT?
IoT offers connections between various devices. It connects objects other than the traditional digital devices such as laptops, phones, and computers. These devices contain sensors and actuators that are capable of storing and retrieving information. A few of the applications of IoT include smart buildings, smart cars, smart homes, and smart wearables.
What is M2M?
M2M offers point to point exchanges of information without internet connection. It also does not require any sort of manual human intervention. M2M communication has been used in telemetry for a long time. M2M was found before the internet of things and hence one could say that IoT improves the functionality of M2M by offering more complicated functions. Some of the applications of IoT are in traffic control and smart agriculture.
History of M2M
There is no original verification for the origin of M2M yet but Theodore Paraskevakos often gets the credit. He is the inventor of transmission of data across telephone lines which lays the ground for modern-day technology of caller IDs.
Nokia was one of the first few companies that used M2M. Later in the years around 2002, it partnered with Opto 22 to provide M2M wireless communication services to users.
M2M magazine was launched in 2003. The publication explains the pillars of M2M communication to be sensors, RFID, remote monitoring, smart service and telemetry.
M2M architecture
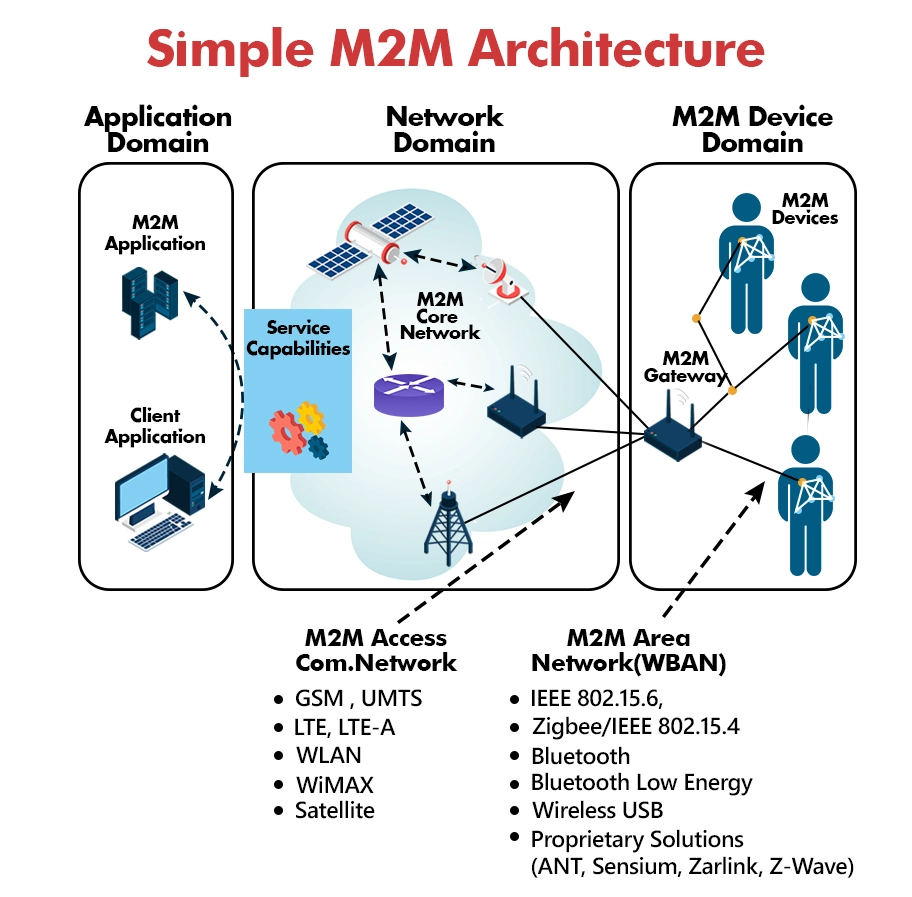
M2M enables machines to communicate with other machines and pass small amounts of information. Some examples could include smoke detectors that detect smoke and send the information to various other digital devices.
M2M and IoT form the foundation of two of the most used technologies in the world and in the future. They are capable of connecting devices to the internet and offer services to business organizations, consumers, and users.
In order to develop and deploy an M2M architecture, we follow the latest standards such as ETSI, ANSI C12, and so on. The three main domains of M2M architecture are:
1. M2M application
As the name suggests, the M2M application domain offers applications to use M2M technology conveniently. Examples include server and end-user applications.
2. M2M network domain
M2M network domain acts as a bridge between the M2M application domain and the M2M device domain. It is made of two parts called the M2M core and M2M service capabilities.
3. M2M device domain
M2M device domain contains all the devices that can connect to the M2M network easily. The device domain can also be called the M2M area network. The M2M device domain includes devices that can connect directly over a network, devices that cannot directly connect to a network and may perhaps require an M2M gateway and proprietary devices.
Working of M2M
M2M devices send data across a network by sensing information. In order to send the data the machines use public networks such as cellular and ethernet.
M2M comprises components such as RFID, sensors, Wi-Fi communication links and automated computer software programs that translate the incoming data to generate responses or actions.
Telemetry is one of the most renowned M2M communication. It has been in use since the beginning of the last century to transmit data. Developers used telephone lines for communication and later moved to radio wave transmission signals in order to monitor the performance of the data that is gathered from remote locations.
The arrival of the internet improved the standards of wireless technology and now wireless communication is used in everyday real life applications such as hospitals, cities, stations, roads and so on.
Key features of M2M
The following are a few of the various key features of the M2M technology:
- M2M consumes lower power as compared to its rival technologies.
- It acts as a network operator and provides packet-switched services
- It is capable of detecting events with the help of its monitoring abilities
- This allows for a delay in the transfer of data
- It allows for the specification to time to send and receive data
- It sends an alert call or wake up call to awaken devices when the device enters an unknown premises
- This continuously receives and sends minimal amounts of data
Applications and examples of M2M
The most common use of M2M is remote monitoring. For example, a vending machine can notify the merchant in case a product is out of stock. M2M is also used in supply chain management and warehouse management systems.
Companies and organizations depend on M2M machines as they use less energy such as oil and gas. M2M machines can also bill users such as smart metres. M2M machines can be used in factories to detect conditions such as pressure, temperature, and equipment status.
In telemedicine, M2M allows remote check up on patients. It allows dispensing medicine and allows doctors to track the health status of patients.
M2M also contributes heavily to financial activities to allow different purchasing options and examples include Google Wallet and Apple Pay.
Smart home systems incorporate M2M communication. It allows devices and home appliances to communicate with each and send message over a network
Finally, M2M also plays a huge part in robotics, traffic management, remote-control software, logistics, fleet management, and automation.
Difference between M2M vs IoT
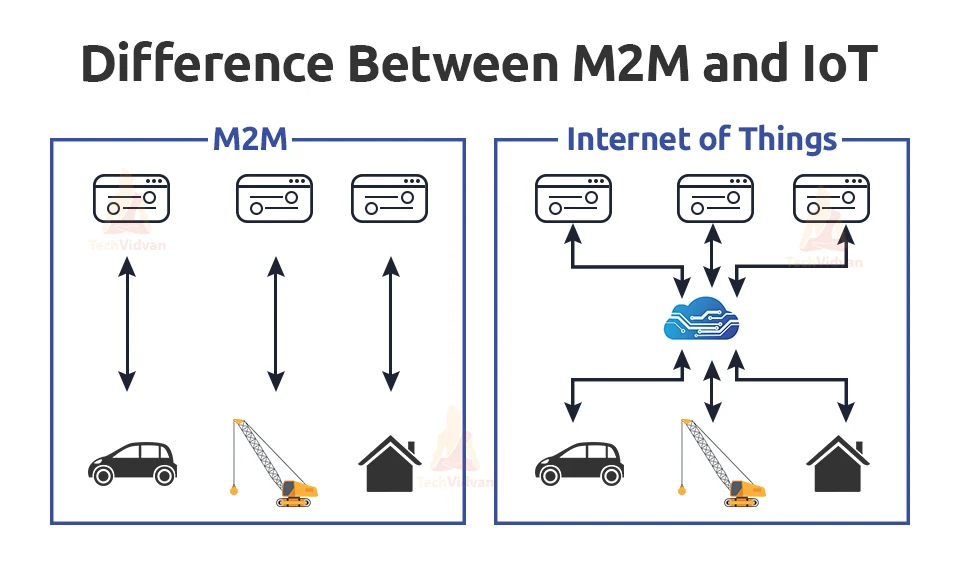
M2M and Iot are similar but they do not exactly perform the same functionality. IoT depends on M2M, but this is not the same vice-versa. Both terms supply device communication but M2M does not need to depend and is single network equipment. Iot on the other hand takes M2M on another level by connecting larger systems on a network that is private or public.
M2M uses communication between machines such as sensors and hardware from one to another whereas IoT uses an IP- network to send and receive data gathered from devices. These devices send the data to large clouds via IoT gateways.
Service management systems rely on data collected from M2M while IoT integrates an enterprise by connecting devices and offering remote monitoring services, this allows organizations to monitor personal assets from a remote location.
IoT provides the end-users with a personal experience and offers them so much more than M2M.
IoT vs M2M
| Topic | IoT | M2M |
| Abbreviation | Internet of Things | Machine to Machine communication |
| Intelligence | Devices include pieces that can make personal decisions without outside interference | Intelligent only to some extent |
| Type of connection used | Devices communicate via a network and other wireless communications | Point to point to communication |
| Communication protocols | TCP/IP protocols such as HTTP, HTTPS, FTP and Telnet | Traditional and less secure communication protocols are used |
| Data sharing | In order to improve the user experience, the data is shared between applications | Data is shared only between allowed connections |
| Internet | IoT is nothing without the presence of internet communication | Devices do not require internet |
| scope | IoT has a bright future and is capable of connecting billions of devices. | Limited scope for devices |
| Examples | Smart wearables, smart cities, smart cars, smart homes and so on | Sensors and data information |
To fully understand the difference between IoT and M2M it is best to understand what machine-to-machine communication does. In M2M data transfers take place without the internet. IoT is a successor of the M2M technology. M2M was found even before the invention of the internet and hence precedes IoT.
Scalability in IoT and M2M technologies
M2M is a traditional mode of communication and the Internet of Things is more stable since it can communicate with various devices within its network and over the internet. Whereas the M2M relies on communication through cellular or wired networks. M2M offers limited possibilities whereas IoT opens a range of possibilities to integrate various devices.
M2M security
There are many security concerns regarding M2M ranging from unauthorized login to hacking and wireless intrusion. Physical security, user privacy, and fraud are also taken into consideration.
M2M security protocols include making devices with devices and machines with non-tampered materials, embedding security into machines, ensuring end to end user encryption and securing database servers.
Another way to make machines more secure is by segmenting machines with their own private networks.
Make a choice between IoT and M2M
M2M is a better option
- If you want your devices to have a point to point communication
- If you want quick communication between a few machines
- When you need your devices to work even without an internet connection
- If you are not concerned about scalability
IoT is a better choice
- If your devices need constant syncing
- If you want your devices to share information between each other constantly
- When you require high scalability and better performance in the management of devices
Requirements
As described the ETSI, European telecommunications standard institute, M2M has the following requirements:
1. Scalability- the M2M must communicate without any errors despite connecting more objects
2. Anonymity- the M2M must not disclose the names of the user and their information when a request is made unless subjected to specific requirements.
3. Logging-M2M must record important activities for example number of failed attempts during installation, defect information, and services not functional. The logs are made available to the user on demand.
4. M2M application communication principles- M2M must ensure dull support in communication of devices on network or through a gateway. It makes use of communication messages such as SMS.
5. Delivery methods- M2M must fully support communication modes ranging from unicast to multicast and analyst.
6. Message transmission scheduling- M2M should manage schedules of messages and should to able to manage the network
7. Message communication path selection-it must be possible to optimize the path of message communication with an M2M system.
Disadvantages of M2M
The most major concerns regarding M2M are all about its security. M2M devices work without the involvement of any human. This directly leads to an increase in the security risks such as hacking, information breaches, cybercrimes, unauthorized logins, and so on.
An M2M system must-have features such as remote management or firmware updates to heal from cyber attacks and illegal attempts to log in.
Summary
So this was it about IoT vs M2M. We looked in detail about M2M, its security concerts, its disadvantages, and its architecture. We hope our explanation was easy to understand.
